Tunneled MySQL Connections
This document explains how to connect to a MySQL or MariaDB database through an encrypted TCP tunnel. We use the mysql command line utility, but the same tunnel can be used by GUI tools.
This example assumes you've already created a TCP route for this service.
Basic Connection
-
Create a TCP tunnel, using either
pomerium-clior the Pomerium Desktop client:- pomerium-cli
- Pomerium Desktop
pomerium-cli tcp aService.corp.example.com:3306 --listen :3306--listenThe
--listenflag is optional. It lets you define what port the tunnel listens on locally. If not specified, the client will choose a random available port.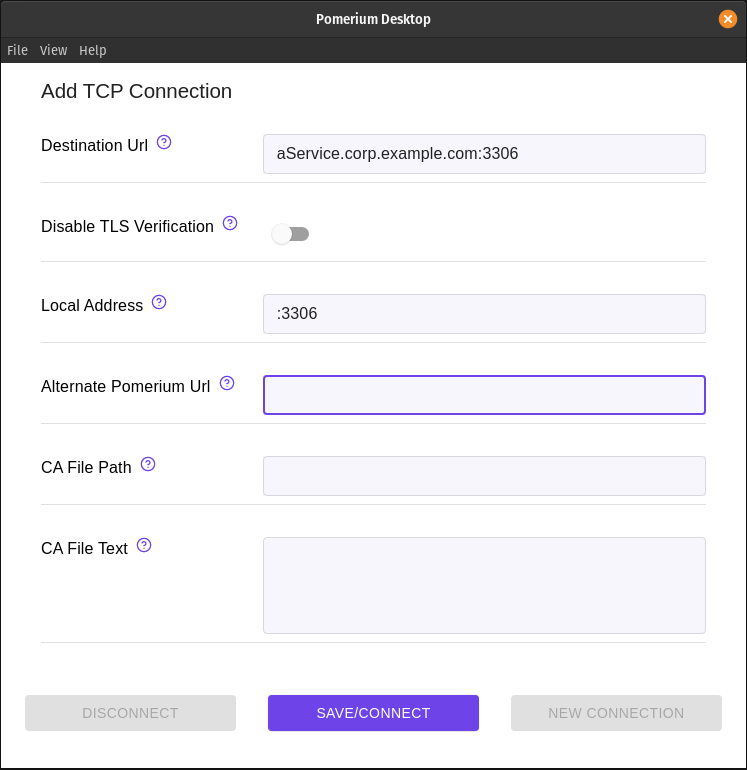 Local Address
Local AddressThe Local Address field is optional. Using it defines what port the tunnel listens on locally. If not specified, Pomerium Desktop will choose a random available port.
-
Initiate your MySQL connection, pointing to
localhost:mysql -h 127.0.0.1 -u USER -p
Allow Access from Remote Hosts:
-
Your MySQL or MariaDB service may not accept connections from remote hosts. Find the
bind-addresskey in the configuration files (usually located in/etc/mysql/) and edit it to accept remote connections. For example:# Instead of skip-networking the default is now to listen only on
# localhost which is more compatible and is not less secure.
bind-address = 0.0.0.0 -
When connecting, you may get an error like
ERROR 1130 (HY000): Host '192.0.2.10' is not allowed to connect to this MariaDB/MySQL server. You can create a user entry in your database for the Pomerium host:CREATE USER 'user'@'pomerium.local' IDENTIFIED BY 'some_pass';
GRANT ALL PRIVILEGES ON *.* TO 'user'@'pomerium.local'Or create a user entry with no host associated:
CREATE USER 'user'@'%' IDENTIFIED BY 'some_pass';
GRANT ALL PRIVILEGES ON *.* TO 'user'@'%'