Ping Identity
This document covers configuring Ping Identity as an IdP for your Pomerium gateway. It assumes you have already installed Pomerium.
While we do our best to keep our documentation up to date, changes to third-party systems are outside our control. Refer to Adding an application - Web application from Ping's documentation as needed, or let us know if we need to re-visit this page.
Create OpenID Connect App
-
To use the Ping Identity provider, first go to the Ping One console and select the environment you want to create the app for.
-
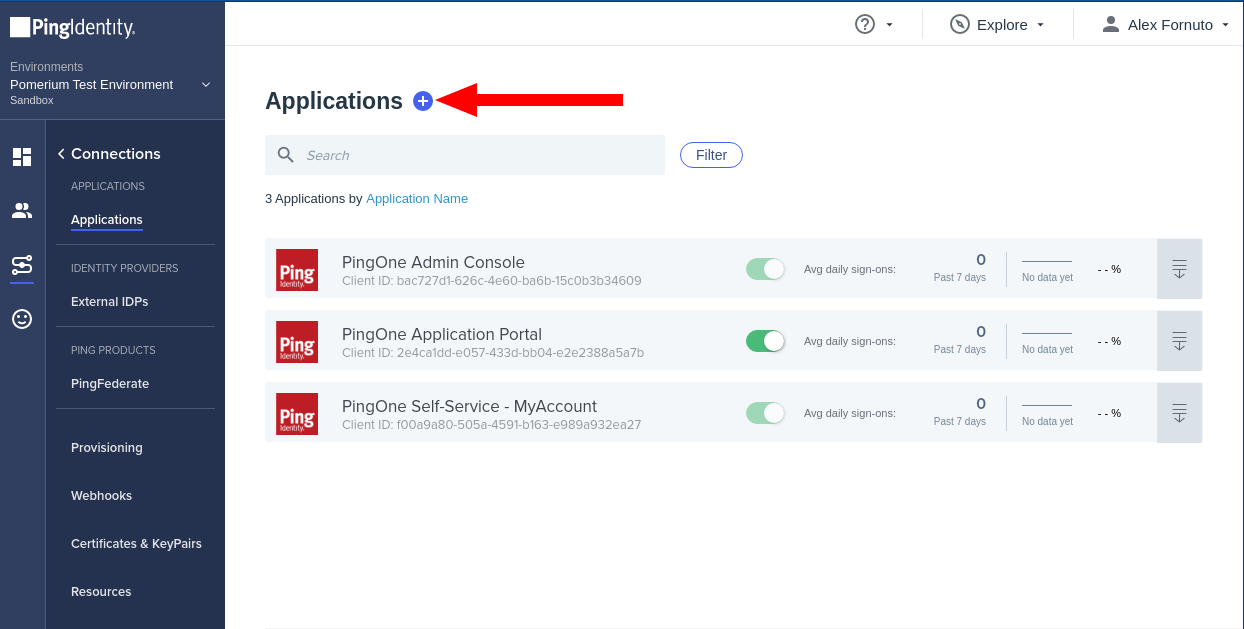
Click Connections in the side menu, select Applications and click + button to create a new application:
-
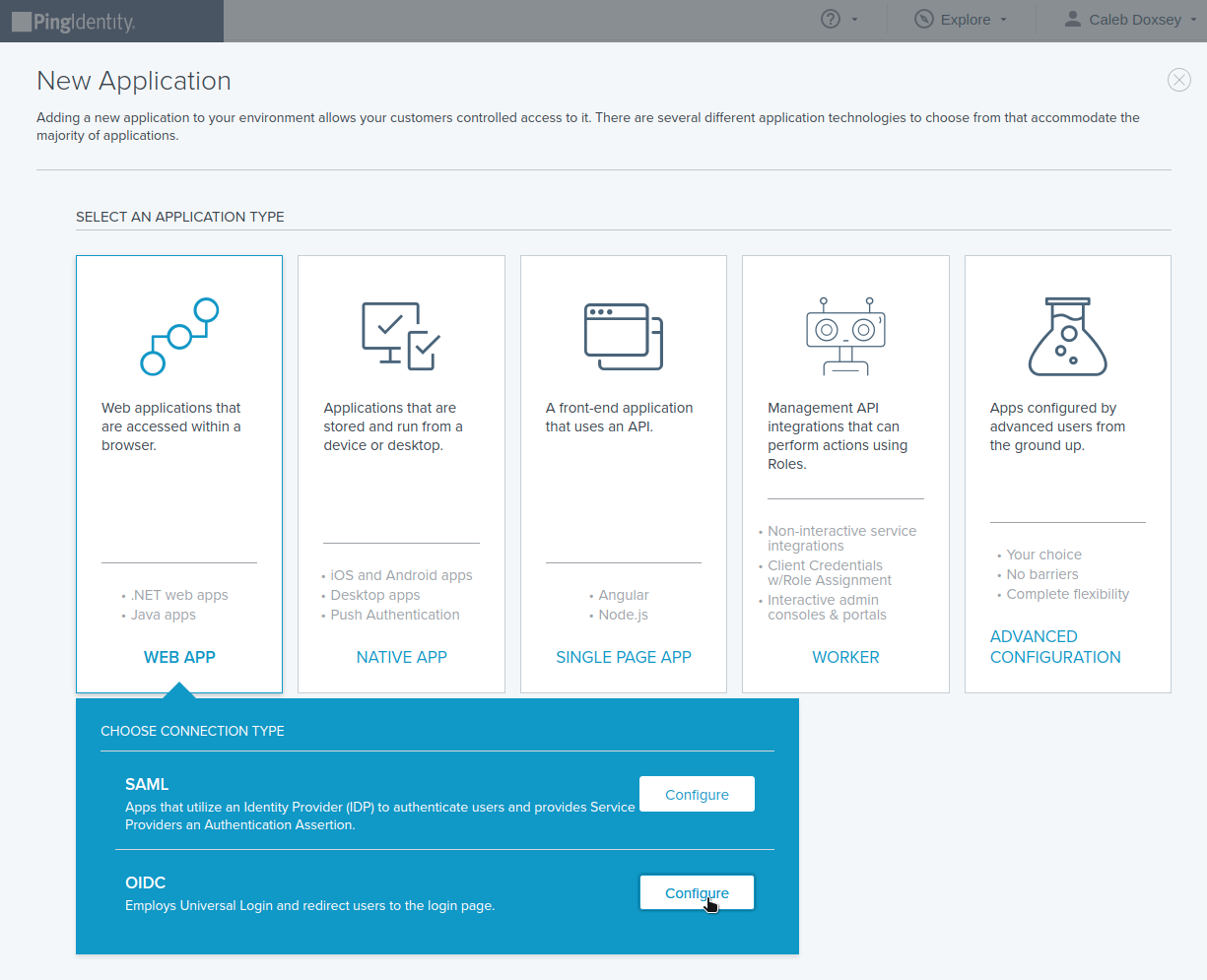
Select WEB APP, then OIDC:
-
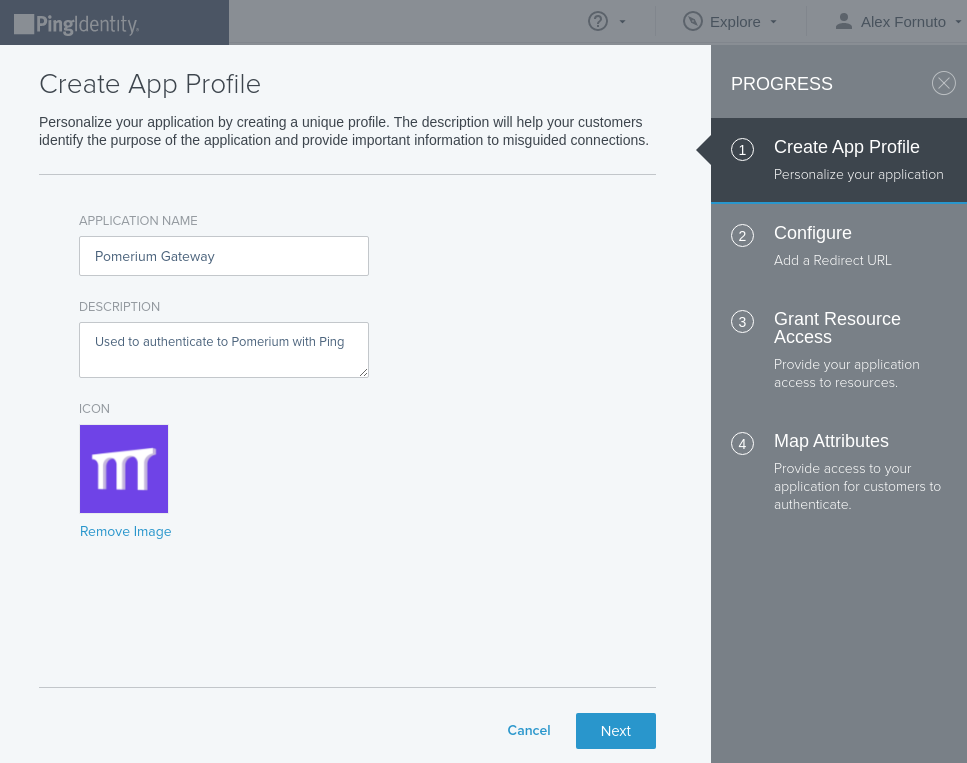
Name the application and optionally provide a description and icon:
-
On the Configure page, add the Pomerium authenticate redirect URL. For example:
https://authenticate.localhost.pomerium.io/oauth2/callback. -
Provide the necessary scopes to your application as needed for your policies from the scopes available in the OpenID Spec. Pomerium requires at least the
emailscope: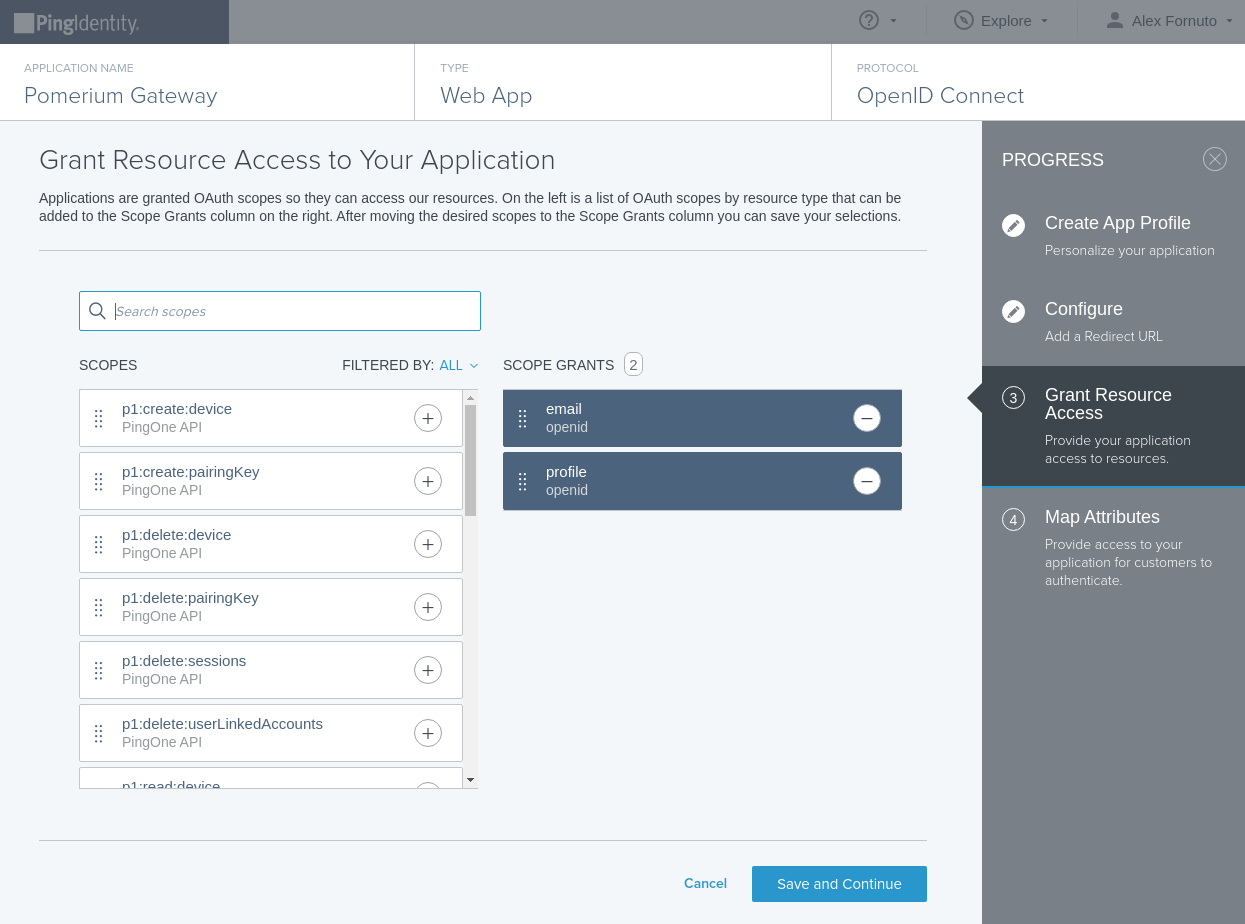
-
OIDC Attributes. Save and Close.
-
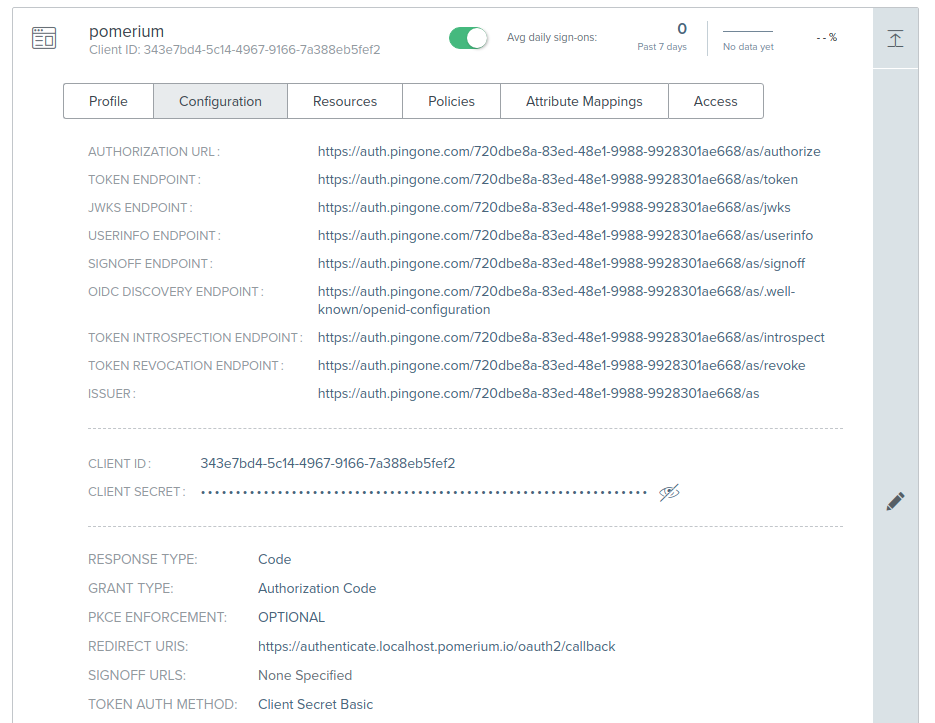
From the Configuration tab of your new application, note the values of the following keys to use in your Pomerium Configuration:
- ISSUER: used as the
idp_provider_url(e.g.https://auth.pingone.com/720dbe8a-83ed-48e1-9988-9928301ae668/as) - CLIENT ID: used as the
idp_client_id - CLIENT SECRET: used as the
idp_client_secret
- ISSUER: used as the
-
Toggle the green slider to enable your new application.
Pomerium Configuration
Update your Pomerium configuration to use Ping as the IdP:
- config.yaml
- Environment Variables
idp_provider: 'ping'
idp_provider_url: 'https://auth.pingone.com/720dbe8a-83ed-48e1-9988-9928301ae668/as'
idp_client_id: 'CLIENT_ID'
idp_client_secret: 'CLIENT_SECRET'
IDP_PROVIDER="ping"
IDP_PROVIDER_URL="https://auth.pingone.com/720dbe8a-83ed-48e1-9988-9928301ae668/as"
IDP_CLIENT_ID="CLIENT_ID"
IDP_CLIENT_SECRET="CLIENT_SECRET"
Groups
- Custom Claim (Open Source)
- Directory Sync (Enterprise)
Custom Claim (Open Source)
A groups claim can be added to tokens returned from Ping by adding it to the "Attribute Mappings":
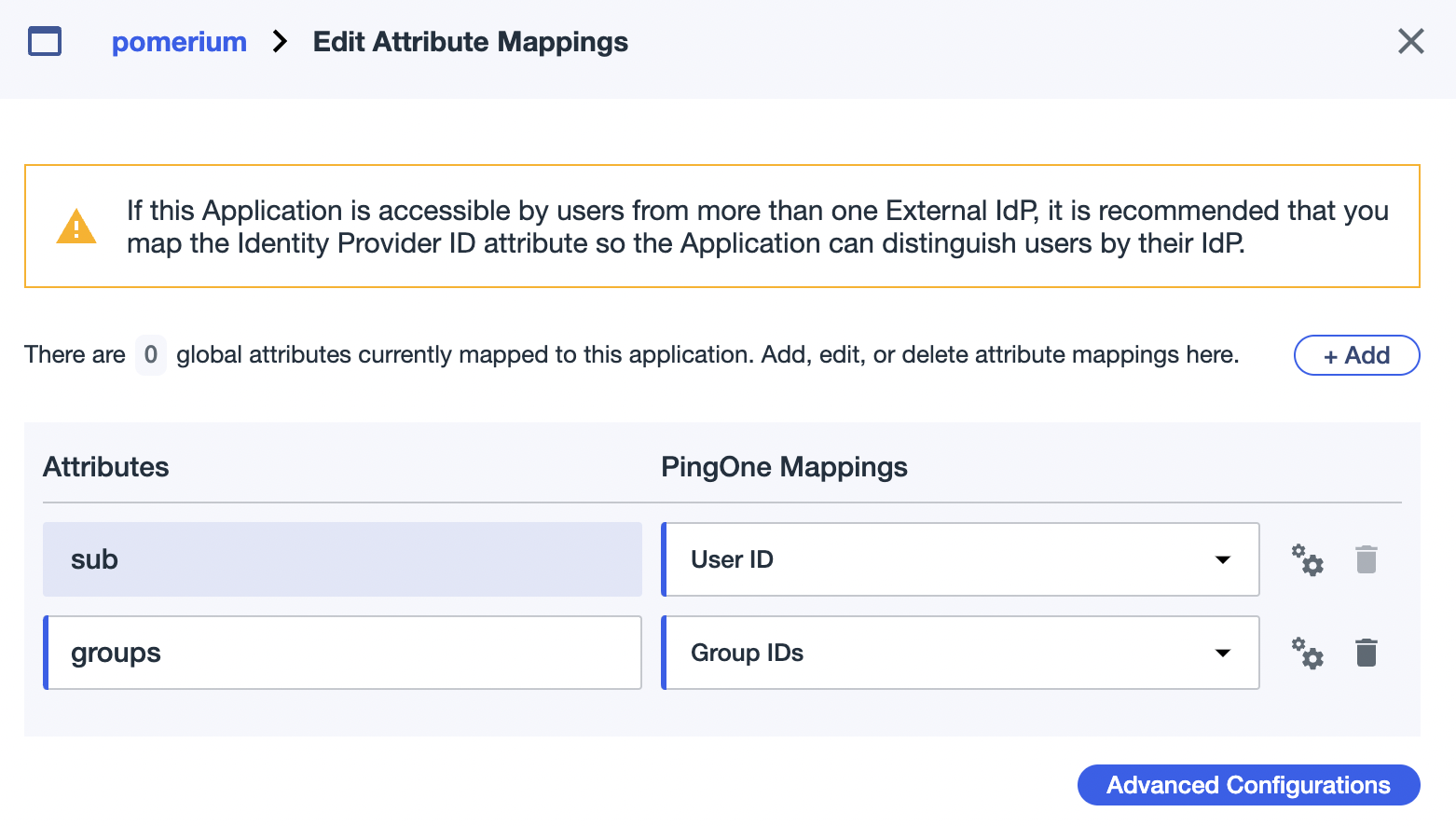
Now when users login they will have a claim named groups that contains their groups and the claim PPL criterion can be used for authorization:
routes:
- from: 'https://verify.localhost.pomerium.io'
to: 'https://verify.pomerium.com'
policy:
- allow:
and:
- claim/groups: 49dfb9e6-f81f-4a1c-b4a3-d0122ebe4aab
The groups claim contains group IDs, not group names.
Directory Sync (Enterprise)
Create a Ping Worker Application
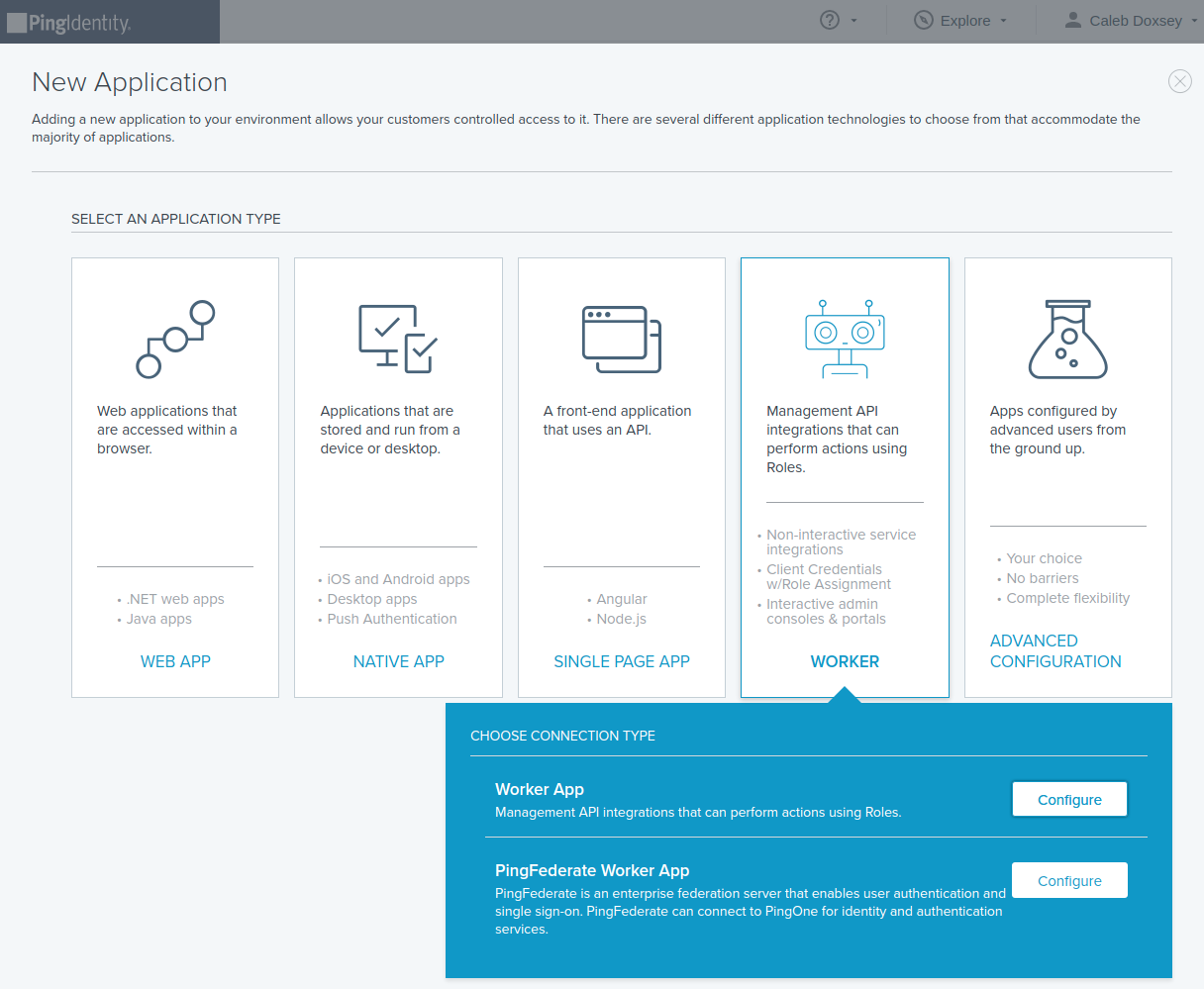
In order for Pomerium to validate group membership, we'll also need to configure a Worker Application in Ping.
-
Click Add Application, and select Worker → Worker App.
-
Toggle the green slider to enable your new application.
-
This application's Client ID and Client Secret will be used in the Pomerium Enterprise Console.
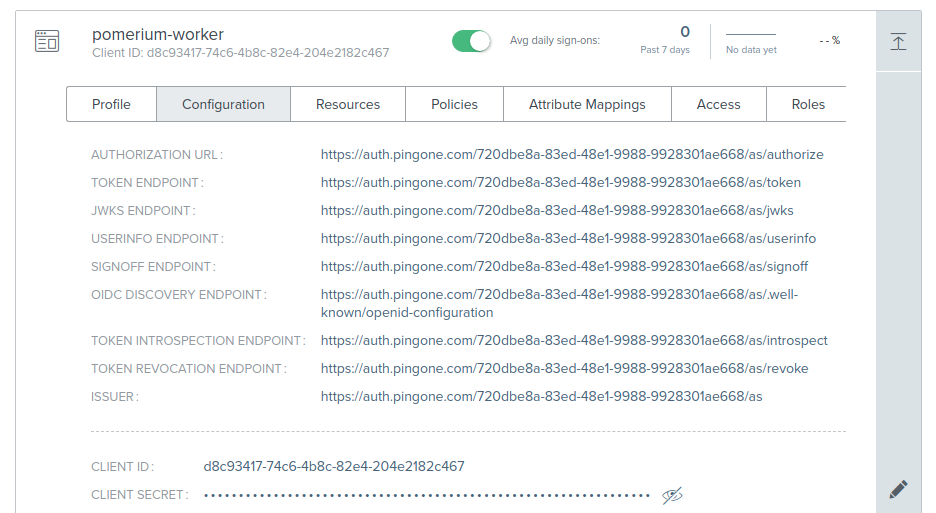
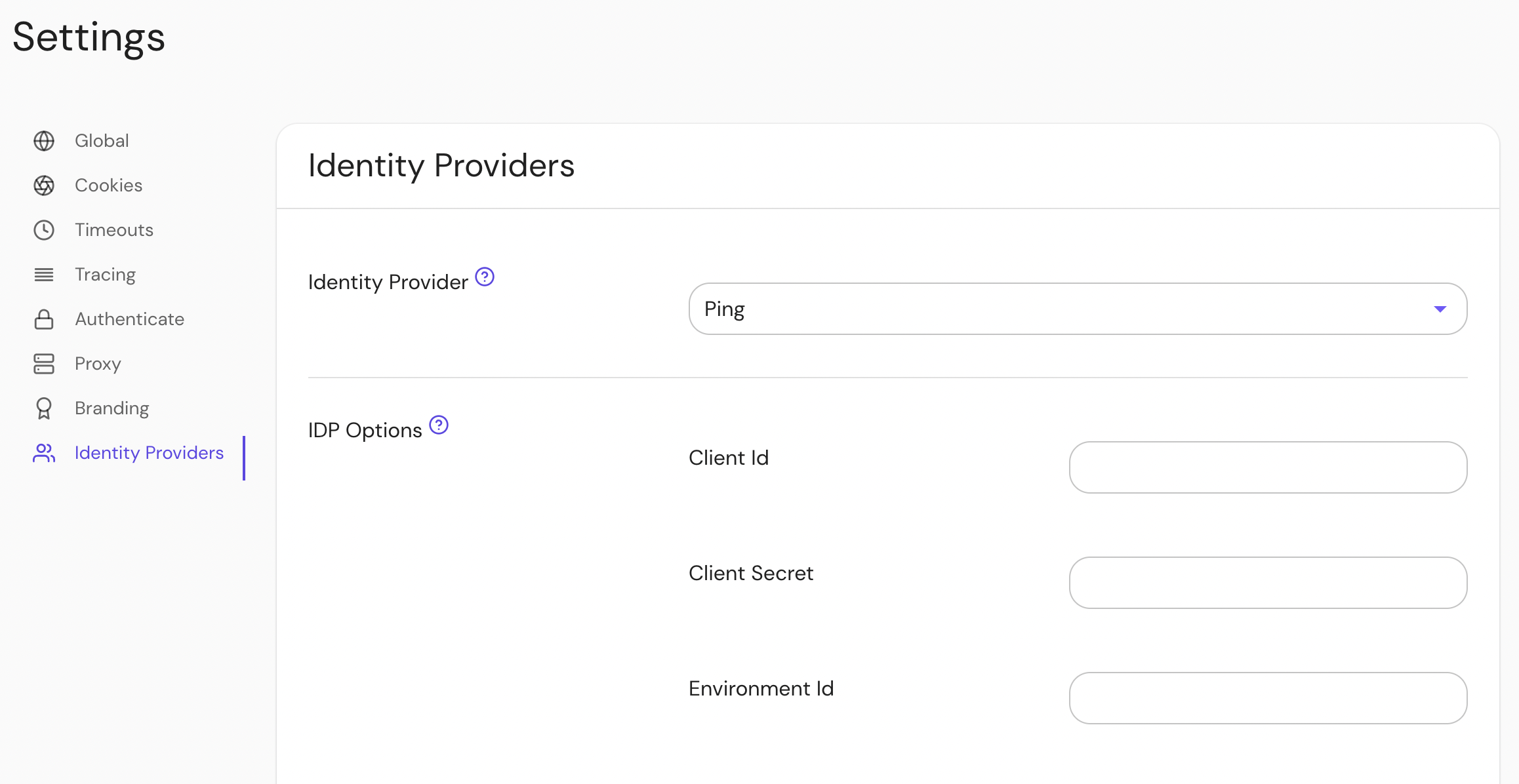
Configure Pomerium Enterprise Console
Under Settings → Identity Providers, select "Ping" as the identity provider and set the Client ID, Client Secret and Environment ID. The Environment ID can be found in Ping under Environment → Properties.
